Title: "Exploring the Future Nexus of AI, Machine Learning, and Cybersecurity"
Abstract:
This project delves into the synergistic relationship between Artificial Intelligence (AI), Machine Learning (ML), and Cybersecurity, envisioning their future trajectory. It explores how advancements in AI and ML are transforming the landscape of cybersecurity, both in defense and offense, and examines potential challenges and opportunities that lie ahead.
1. Introduction:
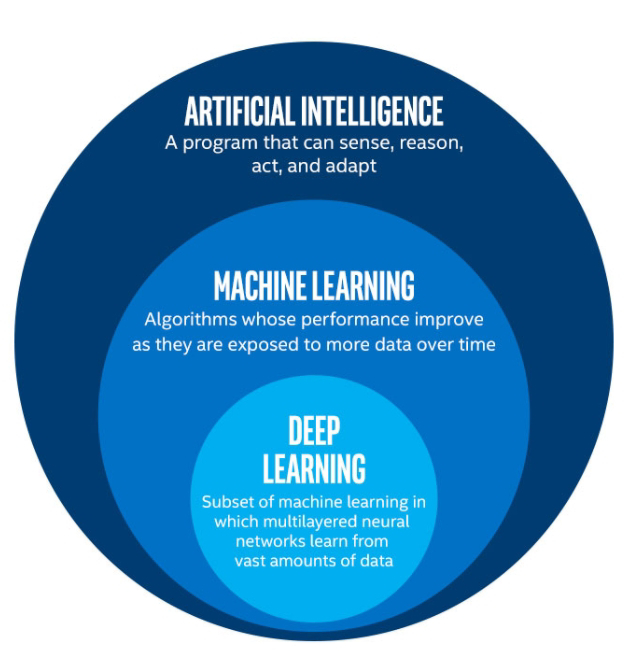
- Brief overview of AI, ML, and cybersecurity.
- Importance of integrating AI/ML into cybersecurity practices.
2. Current Landscape:
- Overview of existing AI/ML applications in cybersecurity.
- Challenges faced by traditional cybersecurity methods.
3. Advancements in AI/ML:
- Deep learning techniques and their impact on threat detection and analysis.
- Natural Language Processing (NLP) for analyzing textual data and identifying threats.
- Reinforcement learning for adaptive cybersecurity defense systems.
4. Future Trends:
- Autonomous cybersecurity systems powered by AI.
- AI-driven threat prediction and prevention.
- Explainable AI for enhancing trust and transparency in cybersecurity decision-making.
5. Ethical and Security Considerations:
- Potential biases in AI algorithms and their implications for cybersecurity.
- Privacy concerns in AI-driven cybersecurity solutions.
- Risks of AI-powered cyberattacks and defenses.
6. Opportunities and Challenges:
- Opportunities for innovation and growth in the AI/ML cybersecurity space.
- Challenges in integrating AI/ML into existing cybersecurity infrastructure.
- Addressing the skills gap in AI/ML expertise within cybersecurity teams.
7. Case Studies:
- Real-world examples of AI/ML applications in cybersecurity.
- Success stories and lessons learned from implementing AI-driven cybersecurity solutions.
8. Conclusion:
- Recap of the importance of AI/ML in shaping the future of cybersecurity.
- Call to action for further research and collaboration in this evolving field.
9. References:
- Citations and resources used in the project.


Comments
Post a Comment